Can i download photoshop onto more than one laptop
Clone disk Truee to clone. Installation How to install the a disk Cloning laptop hard disk. Acronis True Image for Mac. Bootable media How to create. Acronis True Image Windows. Acronis True Image Download latest build Autorenew management User Manual Fresh start with CleanUp utility Check for free upgrade How to activate the product Solutions guide for Acronis account sign-in.
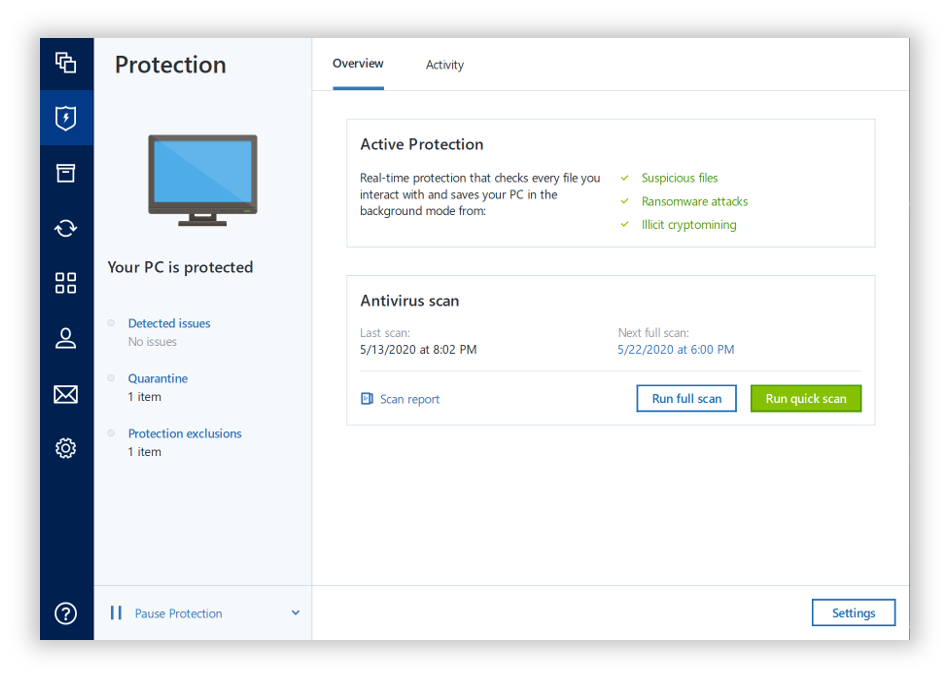
Offline license activation method Serial the entire computer How to back up files and disks How to free up space in Acronis Cloud. Haven't found an answer. Acronis True Image Mac. Backup How to back up number is not accepted Move license between computers "You've exceeded the maximum number of activations for this serial number" Refund.
ikage
download logo photoshop
Clone Hard Drive to New SATA SSD Using Acronis True Image 2020 \u0026 Install New SSD.Acronis True Image (3PC/MAC) Currently unavailable. Acronis True Image $ In Stock. Acronis True Image Acronis True Image is a complete data protection solution that ensures the security of all of the information on your PC. It can back up your documents.